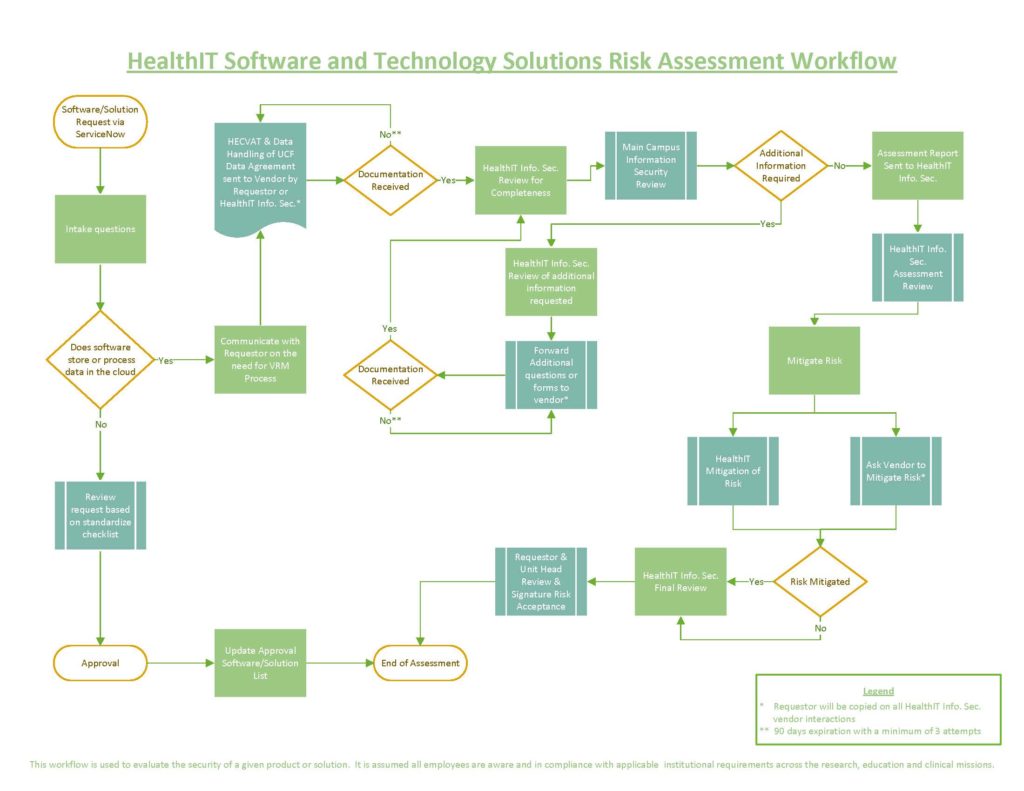
All software and technology solutions that stores or processes data outside of UCF (“in the cloud”) will need to go through the full VRM review process. Additionally, it is assumed all employees are aware and in compliance with applicable institutional requirements across the research, education and clinical missions.
In alignment with university and federal regulations, the Health IT Information Security Office acts as liaison to facilitate the vendor review process for any softwares, prior to use at the College of Medicine and its associated entities. The review is intended to evaluate the risk and implement the appropriate protectants in the technical environment to ensure the safety of our student, patient, and research data.
Per internal HealthIT Standard Operating Procedures (HIT-103, Software Installation), the following minimum data elements are required for compliance with internal procedures and institutional requirements.
- Requestor name
- Targeted user names
- Administrator names
- Business purpose for requesting software or technology solution
- Type of data stored or transmitted
- Approval or denial of request
This information will allow our offices to facilitate the review, as depicted below in the Risk Assessment Workflow.